ERC-20 tokens are among the most frequently stolen assets in the crypto industry, and even some of the updates intended to fix the issues are inadvertently facilitating theft.
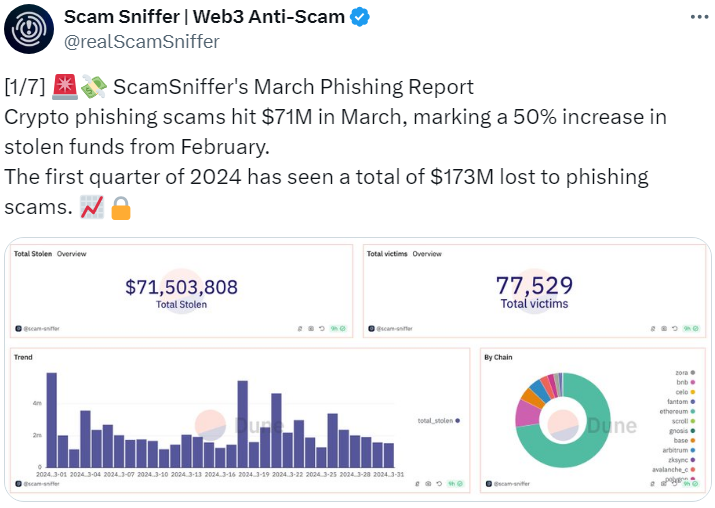
The Ethereum network’s near-ubiquitous token standard accounted for 89.5% of the $71.5 million worth of crypto lost to phishing scams in March, according to Scam Sniffer.
These tokens were stolen as a result of victims unwittingly being phished and approving functions like “permit” and “increaseAllowance.” Functions intended to enhance the token standard’s efficiency have introduced new vulnerabilities.
First introduced back in 2015, ERC-20 tokens are full of gaping security holes, with little chance of a fix any time soon.
“The problem is because of historically bad decisions in ERC-20 and Ethereum designs,” Mikko Ohtamaa, co-founder of algorithmic investment protocol Trading Strategy, tells Magazine.
He says issues related to token design are mainly a problem specific to Ethereum and (to a lesser extent) Solana.
“The issue has been fixed on other chains like MultiversX, Radix, Cosmos-based ones, and so on,” Ohtamaa says.
But the immutable nature of smart contracts complicates efforts to rectify ERC-20’s flaws.
Phishing attacks: Uniswap’s Permit2
Uniswap’s “Permit2” — a smart contract launched in 2022 — aims to improve transactions by allowing users to grant batch token approvals to DApps. This eliminates the need for separate approvals for each transaction, saving gas fees in the process.
Permit2 is similar to its predecessor, “permit” from Ethereum Improvement Proposal-2612, which introduced off-chain token approvals. As these are not on-chain, signing these messages doesn’t incur gas fees.
EIP-2612 is an ERC-20 extension, meaning that it’s an optional feature. But most ERC-20 tokens circulating in the market don’t have this add-on, meaning users can’t always reap the benefits when interacting with DApps.
And that’s where Uniswap’s Permit2 comes in. This intermediary contract extends EIP-2612 to the entire spectrum of ERC-20 tokens on its platform.
But what seemed to be a valuable update for DeFi participants in one of the world’s largest decentralized exchanges prompted one researcher to sound the alarm bells.
About a week after Uniswap’s new contract release in November 2022, security researcher Roman Rakhlin published a Medium article to demonstrate how illicit actors can obtain permit signatures via phishing schemes, ultimately stealing tokens from unsuspecting victims.
“Like a month after I published my article, I saw some drainers that actually started to use permit signatures like I demonstrated,” Rakhlin says.
Uniswap did not respond to Magazine’s comment request.
ERC-20 and cryptocurrency scams
None of which is to say that ERC-20 tokens weren’t a major leap forward when introduced over eight years ago. They provided a generic framework that allowed new fungible tokens to be created on Ethereum and operate smoothly within predefined rules.
The standard’s core functionalities, like the “approve” mechanism, enable tokenholders to manage their assets in decentralized ecosystems and to grant permissions for assets to be moved on their behalf, thereby catalyzing the rise of DeFi.
There is a discrepancy between Ethereum’s native currency, Ether, and ERC-20 tokens, particularly in how they interact with smart contracts.
For one, sending Ether to a smart contract is straightforward. A user simply sends Ether much like they would when sending it to another person’s wallet.
But ERC-20 tokens require approvals when interacting with other smart contracts. Malicious actors can target this confirmation procedure to deceive users into signing fake messages.
“The standard itself is flawed,” Mikhail Vladimirov, an Ethereum developer and smart contract auditor, tells Magazine.

In 2016, Vladimirov authored a paper describing a theoretical “approve” attack vector where changes in approved token amounts could be exploited by malicious entities to move a larger amount of funds than initially permitted by the token owner.
For example, let’s say Alice owns 1,000 tokens and wants to trade them on a DEX. Alice uses the “approve” function to allow the DEX to spend 500 tokens on her behalf. But Alice changes her mind and wants to trade more.
Alice can raise the amount of approved tokens by first setting the allowance to zero and then approving 800 tokens. In this hypothetical scenario, a malicious actor can initiate a transaction in the brief period before the reset to zero and before the new allowance, spending more tokens than Alice intends.
This particular theoretical attack could be quite tricky to pull off as it relies on targeting the short window when Alice amends her approval.
The paper proposed a solution to this hypothetical attack that lets users change the allowance instead of setting a new one.
The adoption of “increaseAllowance” and “decreaseAllowance” functions in 2017 began to address the risk of “approve” attacks by enabling tokenholders to adjust approved token amounts without resetting them entirely.
With these functions, Alice no longer has to reset to zero but can directly change her allowance to 800 tokens.
“The increasedAllowance function is meant to solve this problem, but in the end, it more often creates additional ones for the end-user,” Lev Menshikov, a security researcher at auditing firm Oxorio, tells Magazine.
In a scam, illicit actors may send phishing messages asking users to increase their token allowance for seemingly valid reasons — like a phony update that requires higher allowances for users to continue enjoying services without disruptions or a fake security measure that requires users to increase approved tokens.
This allows the hackers to move the approved tokens from the user’s wallet to theirs, draining the entire amount in some instances.
ERC-20 tokens: The immutable curse
IncreaseAllowance was removed from the ERC-20 contract last year and moved to an extension after independent security researcher pcaversaccio raised concerns about scamming possibilities enabled by the function.
“Since contracts are immutable, you can’t change them,” pcaversaccio tells Magazine.
For existing tokens already in circulation — and there are untold numbers of them — modifications are not feasible due to blockchain’s immutable nature.
However, by utilizing upgradable proxies or intermediary contracts, projects have the capability to augment or diminish functionalities, such as eliminating non-core functionalities like “increaseAllowance” and “permit,” akin to how Uniswap’s Permit2 brought the “permit” function to ERC-20 tokens lacking this capability on its own.
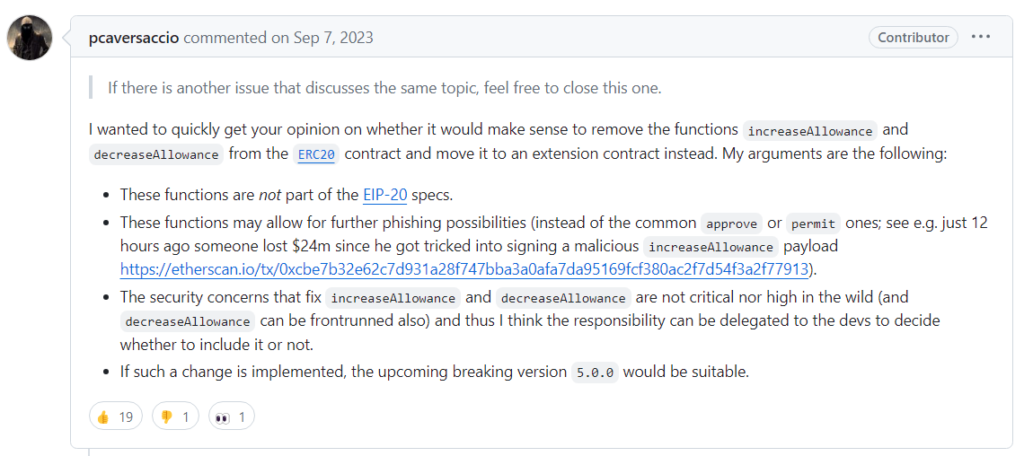
But pcaversaccio adds that the “approve” function must be kept since it belongs to the original ERC-20 specification.
That means the attack vector will remain pretty much forever.
“Immutability is a feature, not a bug on the execution layer.”
The issue is on the application layer, he says — like DApps and wallets.
Vladimirov concedes there are flaws in the ERC-20 design but attributes the rise in scams primarily to social engineering — manipulation tactics that trick the humans who interact with security systems rather than the technology itself.
He argues that wallets should provide simpler or human-readable formats rather than technical jargon or codes that often confuse users and make them more susceptible to scams.
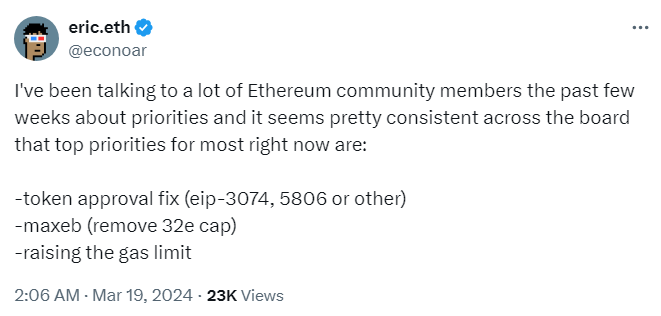
“Unfortunately, we can’t require all of the [wallets] to do things in the right way, especially if the community can’t agree on what is the right way,” Vladimirov says.
Ohtamaa suggests the security community does not consider scams a high-priority issue as they mainly affect lower knowledge users or are caused by faulty front ends.
“Some security researchers are even more arrogant to say it’s ‘a stupid user issue’ or something ‘wallet and front-end developers should fix’ pushing the problem they caused to someone else,” Ohtamaa says.
Phishing attacks catch out crypto OGs
Increasingly though, anyone and everyone transacting regularly in the Ethereum ecosystem is starting to fall victim to the ubiquitous scams.
Even crypto natives, such as Necksus, a crypto miner and collaborator with the forensics platform Intelligence On Chain, have fallen victim to sophisticated social engineering tactics.
“The losses were severe, but I am slowly working to have them recovered,” says Necksus, who claims to have lost approximately $20,000 to a phishing scam.
Necksus says he was tricked by a compromised account of an NFT artist and visited the website of a fake Web3 social media project.
“I did not know it until it was too late,” he adds.
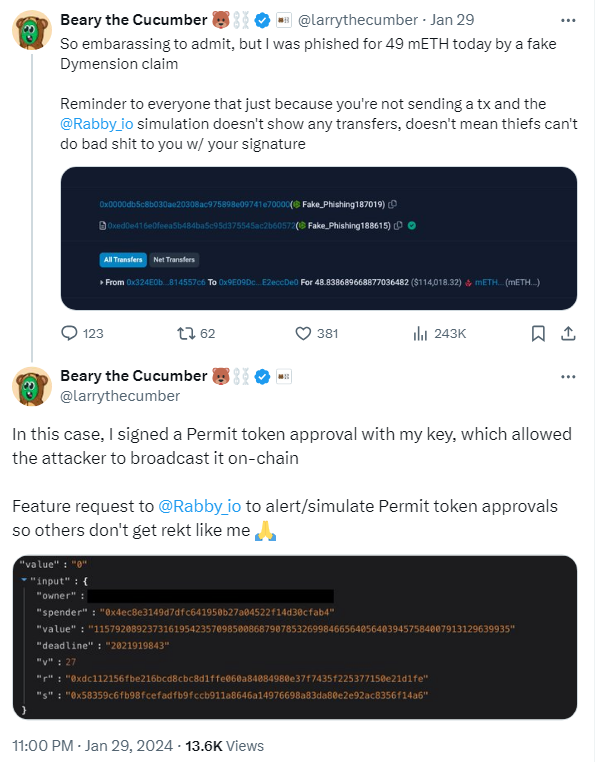
The co-founder of the DeFi platform Pickle Finance, who operates under the pseudonyms “Larry the Cucumber” and “Beary the Cucumber,” also fell victim to a recent phishing scam that involved the “permit” function.
Unlike most victims, Larry the Cucumber used additional precautionary measures, such as using a transaction simulator that allows users to review the scenario before finalizing the transaction.
Menshikov of Oxorio warns investors that inventive new phishing trends continue to appear.
“A really important trend that I could highlight in the field of phishing is the noticeable popularization of attacks on ENS Domain owners,” Meshikov says.
In this phishing scheme, attackers send fake email alerts to ENS domain owners to lure them to a fake renewal site where their funds can be extorted.
Vladimirov claims that the immutability of smart contracts and the constantly growing amount of tokens makes it difficult for any on-chain solutions to prevent attacks and notes social engineering tactics (AKA conmen and tricksters) existed long before crypto.
Instead, he says that the real solutions will come from the evolution of security tools that can warn users of known attack vectors.
Larry the Cucumber tells Magazine that crypto users can protect themselves from many attacks by using security tools like WalletGuard and Pocket Universe, where users can scan URLs to detect risks such as wallet drainers.
Pcaversaccio’s general rule to avoid phishing scams is to be suspicious of everyone and everything: “Be paranoid about everything you sign.”
But Ohtamaa takes the somewhat cynical view that there is more money to be made by “not fixing the issue.”
“It is always more profitable to sell aspirin than to cure the patient,” Ohtamaa says.
week.

The post Ethereum’s ERC-20 design flaws are a crypto scammer’s best friend appeared first on Cointelegraph Magazine.