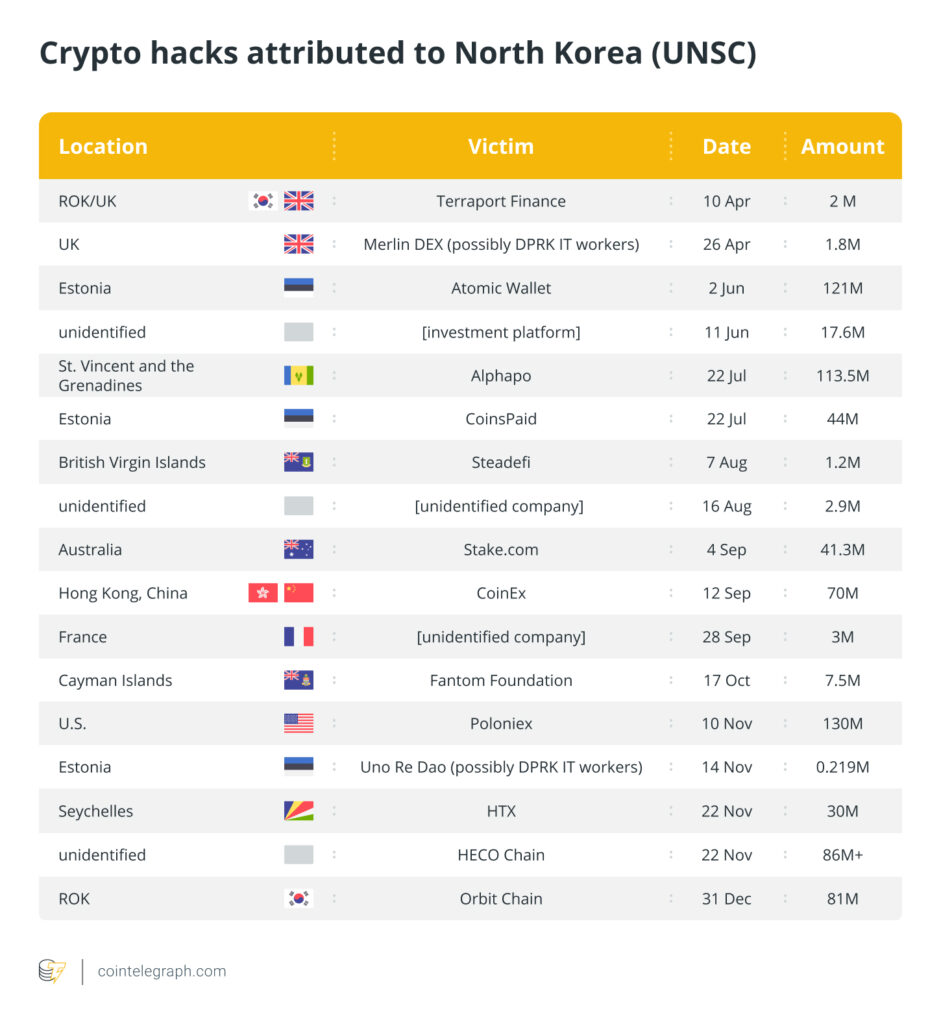
More than 70% of the crypto lost to North Korea-linked hacks since 2020 was stolen via private key exploits, according to Magazine’s analysis of data from the United Nations Security Council (UNSC) and DeFiLlama.
The combined figures suggest North Korea was responsible for about $2.4 billion of crypto heists since 2020, of which $1.69 billion was stolen due to compromised private keys.
These cybercrimes are often attributed to the Lazarus Group — a notorious hacking syndicate allegedly backed by the North Korean state — and allegedly support the hermit kingdom’s weapons of mass destruction program.
The UNSC published a 615-page report last month detailing probes into 58 crypto heists with suspected North Korean involvement dating back to 2017. The hacks netted approximately $3 billion, including $700 million during 2023 alone.
Gaining a comprehensive picture of every attack is difficult, however. Slava Demchuk, co-founder of blockchain intelligence platform AMLBot, tells Magazine that not all victims report losses and the true scale of hacks could potentially be underestimated.
Blockchain forensics firm Chainalysis estimates a higher figure than the UNSC, reporting in January that North Korea-linked hacks accounted for $1 billion of the $1.7 billion total stolen last year.
In 2020 North Korea denied being responsible for any “cyber threat,” putting it in the same quotation marks as other U.S. criticisms of the country regarding “human rights,” “sponsoring of terrorism” and “money laundering.”
Few outside of North Korea believe that, however, due to the on-chain evidence pointing back to North Korea-linked hackers.
Lazarus Group uses phishing and exploits software flaws
Julius Serenas, the founder of NeurochainAI, tells Magazine that hackers choose their targets wisely and only bother with high-value heists.
“As far as I am aware, North Korea is the only country that executes hacks for monetary gain, so this is no surprise that they are targeting groups where they have higher potential success rate,” he says.
“The code data is available on-chain for everyone to read which gives hackers a lot of information as well as time to execute multiple tactics to exploit any potential vulnerability,” he adds.
According to the UNSC report, North Korean hackers often use phishing tactics and exploit software flaws to steal cryptocurrency, which is then laundered across thousands of addresses.
They utilize crypto mixers and privacy tools to hide their tracks and frequently cash out through the TRON blockchain and Tether (USDT).
Their operations increasingly depend on services from Russia and China, the UNSC adds.
The exploits are notable for their sophistication, resources and time frames.
“[North Korean hackers] focus on a small number of high-value targets and can play a very long game, combining detailed technical knowledge with social engineering and spear-phishing capabilities,” Gonçalo Magalhães, head of security at Immunefi, tells Magazine.
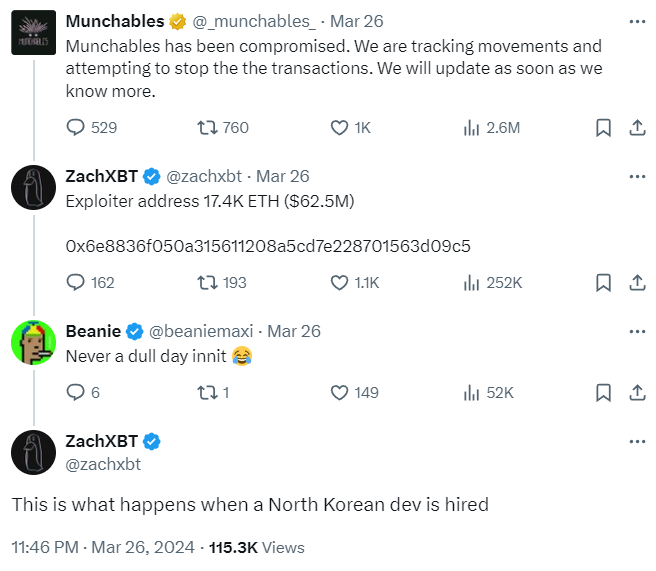
The most recent attack linked to North Korea was the $62.5 million stolen from Munchables late last month by the team’s developer, who has suspected ties to North Korea.
While the funds have since been recovered, it is recorded as the year’s largest heist, representing 44.5% of the total of $140 million.
The importance of high security around private keys
Private key compromises are not only frequent but typically lead to the largest losses, Magalhães says. And that goes for major attacks in general.
Including North Korean attacks, there have been at least 41 major hacks involving private key exploits since 2020, resulting in $2.9 billion in losses, UNSC and DeFiLlama data shows. That’s about 38% of the $7.74 billion in total value hacked since the new decade began.
“A bug in a smart contract might get an attacker to steal a portion of user funds [but] a stolen private key will allow a hacker to withdraw the entire volume of funds or compromise a treasury,” Magalhães says.
Risks related to private keys can target both individuals and protocols. Security experts often advise investors to keep their assets off of centralized exchanges as they are vulnerable to hacks and insolvencies.
However, security concerns extend to the decentralized sphere as well.
Kieran Mesquita, a contributor to the privacy protocol Railgun, notes that many decentralized projects exhibit centralized tendencies due to the management of admin keys. While in the building phase, most DeFi projects retain admin keys to upgrade and recover from serious bugs or flaws. But these keys also leave the protocols vulnerable to attacks.
“Private key hacks often occur due to carelessness on the side of DeFi protocols where mechanisms around upgradability are added as an after-thought due to them not being part of the core protocol function,” Mesquita tells Magazine.
DeFi protocols’ primary focus tends to be on establishing the main features that define the project’s utility, like swaps or lending. As Mesquita points out, when upgradability features are added later, they can create security gaps.
Lazarus Group, Railgun and Vitalik Buterin
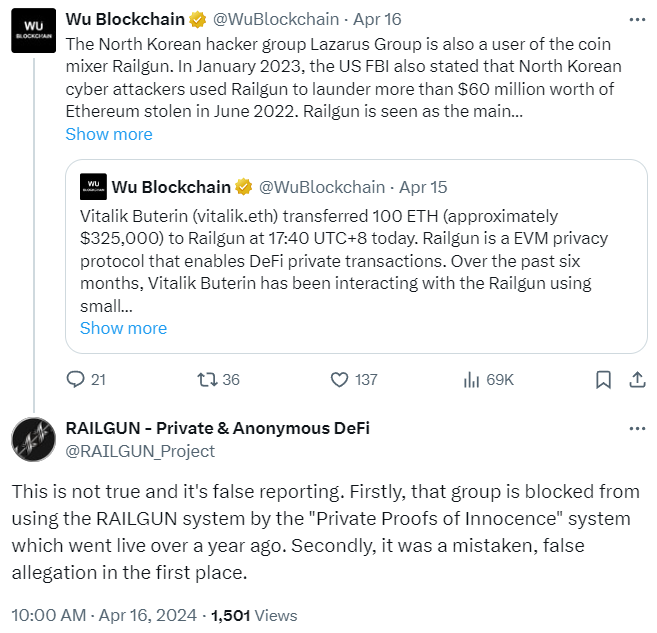
The U.S. Federal Bureau of Investigation in January alleged that North Korean cyber criminals used Railgun — a privacy protocol favored by Ethereum founder Vitalik Buterin — to launder stolen funds.
Railgun denies the claims and says that the group is blocked from using its system.
Private key hacks, leading in volume with $2.9 billion stolen, are the second most frequent type of exploit, with 41 incidents since 2020, according to data from the UNSC and DefiLlama. Flash loan attacks rank first in frequency, with 64 incidents against protocols.
Flash loan attacks allow malicious actors to borrow large sums of cryptocurrencies from DeFi protocols without collateral on the condition that it is repaid immediately.
This sudden access to capital opens doors to market manipulation strategies.
For instance, attackers might exploit existing price discrepancies across different trading platforms.By using the borrowed funds to buy an asset on one exchange where it’s cheaper and then selling it on another where it’s more expensive, they can profit from the price differential, but such large-scale trades can lead to sudden price drops.
Manipulating the market price of an asset can impact smart contract functions that rely on price feeds for operational decisions, such as those managing loans, swaps, or liquidity pools.
Since 2020, flash loan attacks have resulted in a lower total loss of $1.16 billion.
“Flash loan attacks, while being common in the DeFi sector, exhibit certain characteristics that make them both relatively easy to execute and typically result in lower average losses compared to other types of security breaches like access control or private key hacks,” Demchuk says.
North Korean hackers don’t have a flash loan attack on DefiLlama records and the UNSC’s report, although there are a few suspected cases.
Last year, a $200 million flash loan attack on DeFi lending protocol Euler Finance involved the hacker sending a small portion of the funds to the Lazarus Group’s wallet, according to Chainalysis. However, after a phishing attempt by the North Korean syndicate against the Euler Finance hacker, the stolen funds were returned, suggesting the transaction was intended for misdirection.
“With a flash loan, anyone can perform an attack as if they had as many funds as a state-sponsored hacker,” Magalhães says.
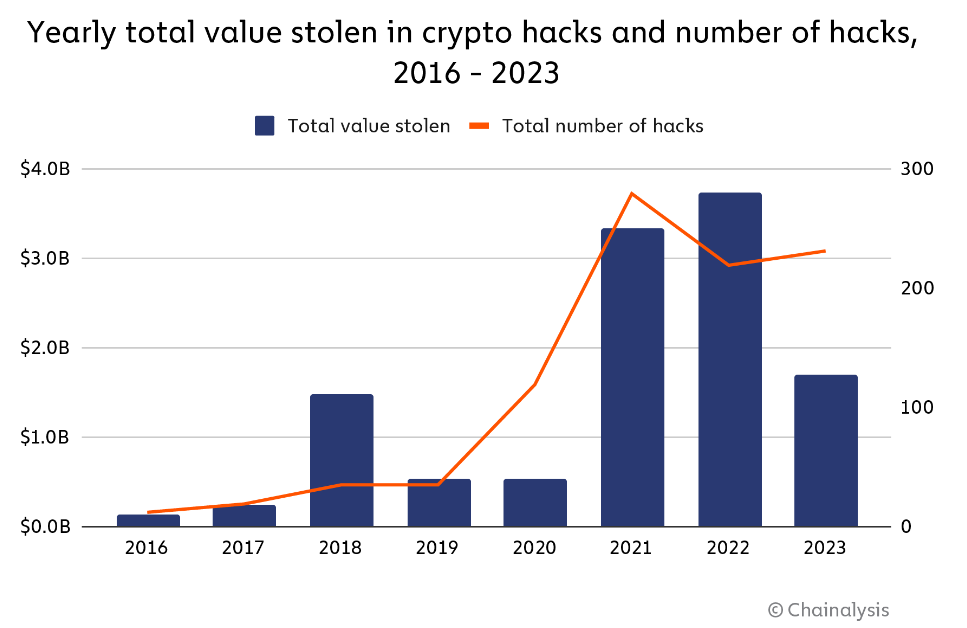
Lazarus Group-linked hacks increased in 2023 but were less profitable
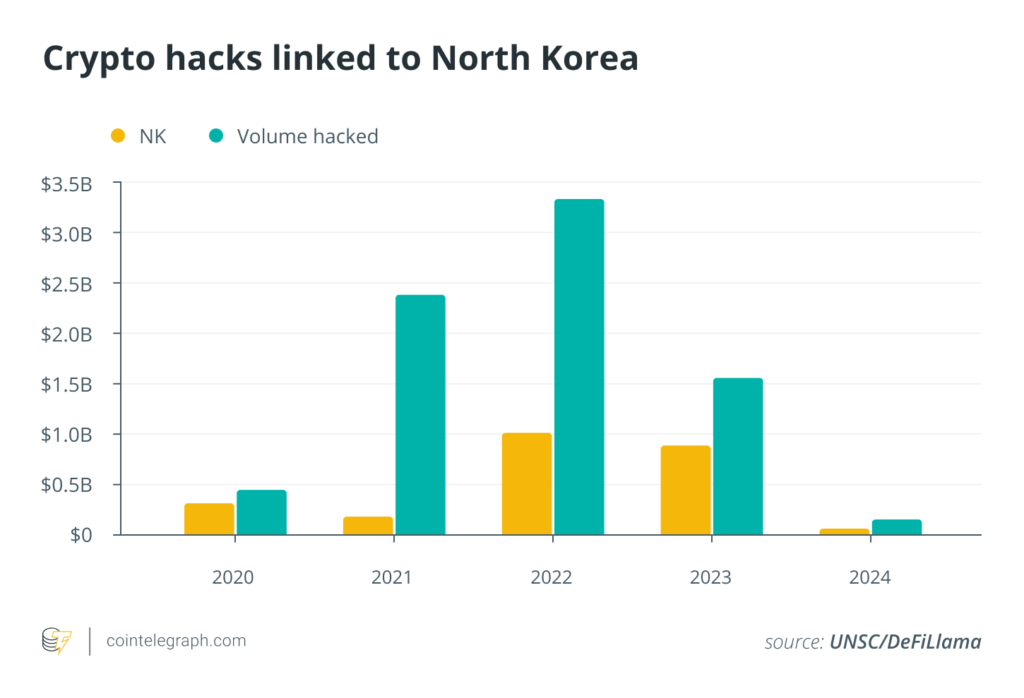
According to Chainalysis, North Korean hackers were more active in 2023 but got away with $700 million less than the year before.
The overall amount of crypto hacked from protocols also dropped to $1.53 billion last year from $3.28 billion in 2022, according to Magazine’s analysis of DefiLlama and UNSC data. The 2023 figure is also lower than 2021’s $2.34 billion. This could indicate that projects are either getting smarter about security, that bear market prices impacted the total or a combination of the two.
DeFi platforms accounted for most of the hacks, and Demchuk says the declining total losses could hint at enhancements in DeFi security. However, he warns investors that hacking volume is expected to increase with favorable market conditions and the growing DeFi sector.
Individual users at risk from phishing attacks
Meanwhile, Tim Zinin, chief marketing officer of 1inch Hardware Wallet, tells Magazine that individual investors are also at risk from exploits.
“The growth in losses from phishing attacks targeting individuals is concerning and likely reflects attackers following the money as more retail users enter DeFi,” Zinin says
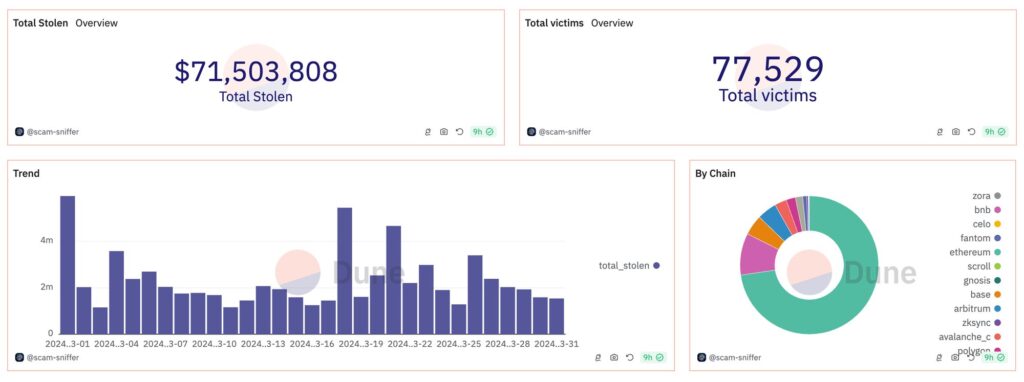
Investors lost $71 million to phishing scams in March, which is a 50% increase from February this year, according to Scam Sniffer.
Railgun’s Mesquita recommends users take it a step further and reduce “blind signing” transactions from their wallets when interacting with DeFi protocols.
Reducing blind signing of transactions can be challenging for everyday users, as many transaction requests appear in code that is difficult to understand. Serenas from NeurochainAI believes that artificial intelligence can help bridge this gap.
“[Blockchain projects] could easily employ AI solutions to analyze and provide security index of a particular project before the user confirms any transaction,” Serenas says.
“AI does not sleep, does not eat and can learn new threat tactics with ease.”
week.

The post Lazarus Group’s favorite exploit revealed — Crypto hacks analysis appeared first on Cointelegraph Magazine.
