Crypto-Sec is our bi-weekly round-up of crypto and cybersecurity stories and tips.
Phish of the week: Turbo Toad enthusiast loses $3,600
Memecoin collector and X user Tech on Ivan lost over 1 million TURBO, worth over $3,600 at the time, when he became the victim of a phishing attack, according to a post he made on July 11. “I’m completely devastated,” Ivan stated.
He lost the tokens after receiving a phishing email containing a link he subsequently clicked on. Ivan did not explain what happened after clicking the link, but he was most likely sent to a malicious web app connected to a drainer protocol.
Blockchain data shows that two separate wallet-draining transfers were conducted against him. The first drained 863,926 TURBO ($3,113.45) and sent it to an address ending in Aece. The second drained 152,458 TURBO ($549) and sent it to a known malicious address that Etherscan labels “FakePhishing 328927.”
Given that the second transfer was much smaller than the first, the “FakePhishing” address probably belongs to the drainer software developer, whereas the “Aece” address is more likely to be owned by the person who conducted the scam. Drainer software developers usually charge a small percentage of the stolen loot as payment for allowing scammers to use their service.
The user had previously called the “increase allowance” function on the Turbo contract, giving an unverified smart contract address ending in 1F78 as the “spender” and authorizing it to spend a large number of tokens. The attacker later used this malicious contract to drain the tokens.
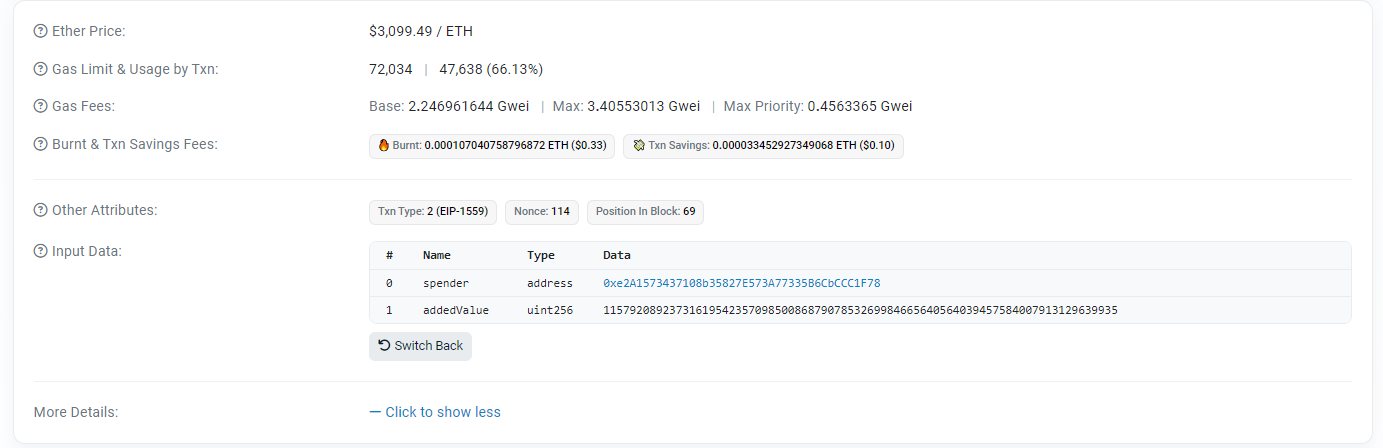
Because the user had previously authorized the malicious contract, the Turbo contract recognized it as legitimate and failed to block the attack. According to his statement, Ivan did not know he was authorizing his tokens to be spent by a malicious app when he initiated this transaction.
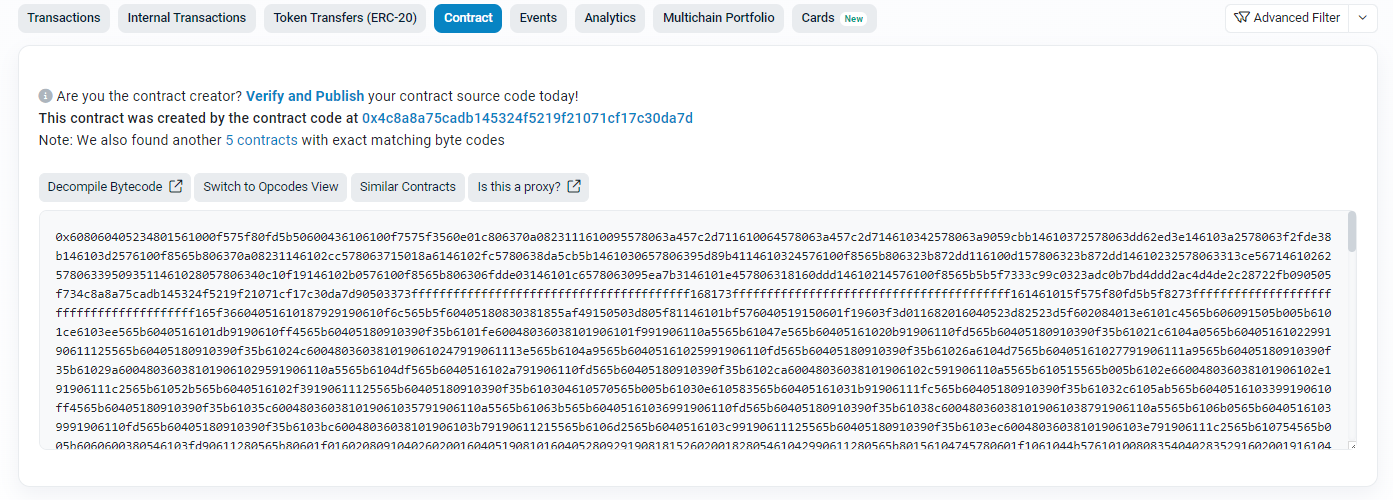
The malicious contract shows only unreadable bytecode on Etherscan, and its functions are not available in human-readable form.
A phishing attack is a type of scam where the attacker poses as a trusted source and tricks the victim into giving away private information or performing an action the attacker wants them to perform. In this case, the attack tricked the user into unintentionally authorizing an app to steal the tokens.
Crypto users should be aware that some Web3 apps are malicious and exist for the purpose of stealing users’ tokens. Users may want to carefully inspect each wallet confirmation when they approve transactions and avoid making token authorizations to apps that haven’t proven their trustworthiness.
Many wallet apps attempt to warn users when malicious sites ask them for token approvals. However, these warning systems sometimes block legitimate sites as well.
White-Hat Corner: Microsoft patches another zero-click Office bug
Microsoft has patched another “zero-click” security vulnerability in its Office Suite, according to a July 10 report from Infosecurity Magazine. The vulnerability could have allowed an attacker to run malware on a user’s machine without requiring the user to download a file. Instead, the user would have only needed to open an email to have their device infected. For this reason, it is called a “zero-click” vulnerability.
The new vulnerability was discovered by Morphisec, the same security team that found a previous zero-click vulnerability in Office products in June. But unlike the other vulnerability, this new one only allowed a zero-click attack from a “trusted sender.” If a sender were untrusted, the attack would have required the user to make a second click.
According to the report, Microsoft claimed that the new vulnerability was more complex and less likely to be exploited than the previous one. Even so, it eliminated the attack vector through a patch on July 9.
Getting infected with malware can be devastating. Once a device is infected, the attacker can often use the malware to steal the user’s keystore file and access their cryptocurrency account. Keystore files are encrypted, so having a strong password can help protect against this threat, but some malware also contains keylogging software that can record a password while it is being typed.
Using a hardware wallet can also help defend against this threat, as the attacker can’t steal a keystore file if it isn’t on the device. But users who rely on software wallets should be aware that zero-click vulnerabilities are starting to become more prevalent. As a result, they may want to avoid opening emails from untrusted sources, even if they don’t plan to click on links or files within the email.
CEXs: Evolve Bank suffers data breach
This week’s CEX report concerns the crypto-friendly Evolve Bank & Trust. Evolve is partnered with crypto payments app Juno and previously provided debit cards to the users of now-bankrupt crypto firms FTX and BlockFi.
According to an official statement from the bank, a hacker entered Evolve’s database on July 8 andleakedcustomer data. Blockchain security firm Veridise estimates that over 33 terabytes of data were stolen in the attack and more than 155,000 accounts were affected.
According to the bank, the cybercriminal group LockBit was responsible for the attack. The group convinced an Evolve employee to click a “malicious internet link.” As a result, the attackers gained access to customer information and encrypted some data to prevent the bank from using it. However, the bank used its backups to restore most of the lost information, so the only significant damage was the customer data leak.
Evolve said the attackers offered to keep the data from being leaked in exchange for a ransom. However, the bank refused.
The attackers now have customers’ “names, Social Security numbers, bank account numbers, and contact information” as well as other “personal information,” Evolve stated. In addition, customers of Evolve’s Open Banking partners also had their information leaked. The bank is still investigating to determine all of the data that was compromised.
No funds were lost in the attack, the bank claimed.
Evolve stated that it has taken steps to shore up its security practices to ensure a breach like this never happens again. In the meantime, it encourages customers to “remain vigilant by monitoring account activity and credit reports” and to be on the lookout for future phishing attacks directed against them.
These potential attacks may involve phone calls or emails pretending to be trusted companies and asking for personal information. Evolve also suggested that customers use two-factor authentication for their online accounts, as the attackers may attempt to use customers’ data to gain access to their accounts on other platforms.
week.

The post Crypto-Sec: Evolve Bank suffers data breach, Turbo Toad enthusiast loses $3.6K appeared first on Cointelegraph Magazine.