Crypto-Sec is our bi-weekly round-up of crypto and cybersecurity stories and tips.
Biggest phish of the week: TAO holder loses $11.2 million
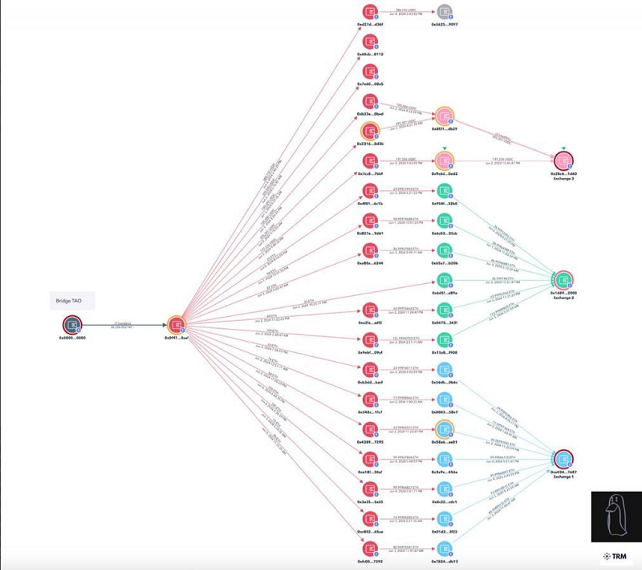
In the largest reported phishing attack so far in June, a user of the Bittensor (TAO) artificial intelligence platform lost over 28,000 tokens worth $11.2 million at the time. The attack was reported by onchain sleuth ZachXBT through his Telegram channel.
The attacker split up the funds into 18 different wallet accounts, which then consolidated them into 16 accounts, ZachXBT reported. Afterward, the 16 accounts bridged the tokens from the TAO network to Ethereum and swapped them for ETH and USDC stablecoin using three different decentralized exchanges.
Splitting up funds into multiple wallets and then recombining them is a common tactic of scammers and is designed to circumvent money laundering detection systems on centralized exchanges. It is this pattern of splitting and recombining that apparently led ZachXBT to conclude that this was a phishing attack.
A crypto phishing attack is a type of scam in which the attacker creates a fake website that appears to be part of a legitimate protocol, such as a decentralized exchange or lending app. But the site is, in fact, malicious and not authorized by the legitimate protocol’s team. When the user authorizes their tokens to be spent by the fraudulent app, it steals them instead of doing what the user expected.
Phishing scams are one of the most common ways for crypto users to lose their funds from an attack.
White hat corner: Microsoft patches “zero-click” vulnerability
According to Security Week, Microsoft has patched a vulnerability that could have allowed attackers to execute code on Outlook users’ devices without requiring them to download or execute a file. Cybersecurity firm Morphisec reportedly discovered the flaw.
The potential attack only required the user to open a malicious email rather than needing to download or run a file. For this reason, Morphisec referred to the flaw as a “zero-click vulnerability.”
Morphisec reported that the flaw allowed attackers to “exfiltrate data, gain unauthorized access to systems, and perform other malicious activities.”
Crypto software wallets use key vault files stored on the device to sign transactions, so these files could potentially have been stolen through such an attack and led to crypto losses.
Despite Microsoft’s patch, some devices may still be running older versions of Outlook, so “[u]sers are advised to update their Outlook clients as soon as possible,” the report stated.
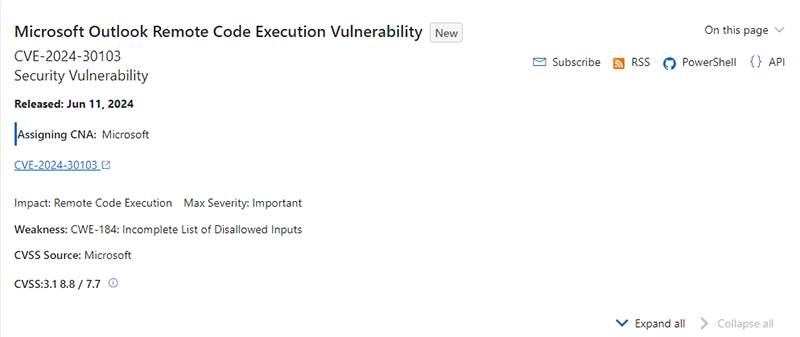
Microsoft listed the vulnerability as “important” but did not label it as “critical.” The flaw affected earlier versions of Outlook 2016, Office LTSC 2021, 365 Apps for Enterprise, and Office 2019, but the most current versions of these apps are not vulnerable.
DeFi exploit of the week: UwU Lend gets exploited twice
DeFi protocol UwU Lend On Ethereum was exploited twice by the same attacker over a period of three days. The first attack occurred on June 10 and drained $20 million from the protocol, while the June 13 second attack drained an additional $3.7 million, according to reports from blockchain security platforms Peck Shield and Cyvers.
In a June 12 X post, the team acknowledged the first attack, stating that the attacker had manipulated the price oracle for Ethena Staked USD (sUSDe), but the team patched the vulnerability once it was discovered. “The team has now identified the vulnerability, which was unique to the sUSDe market oracle and has now been resolved,” it claimed.
According to blockchain security platform Peck Shield, the attacker manipulated the sUSDe oracle used by the protocol, causing it to show false prices. This allowed some liquidity pools to lend $20M more than they otherwise would have been able to. The attacker then pocketed these funds for themselves and did not pay back the loans.
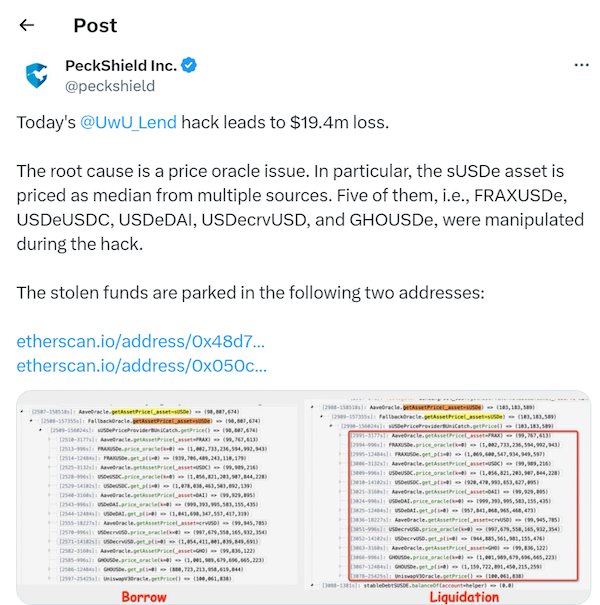
To explain in more detail: The protocol’s sUSDe oracle used an average price derived from multiple liquidity pools. Using large flash loans, the attacker was able to change the prices in four of these pools: FRAXUSDe, USDeUSDC, USDeDAI, USDecrvUSD and GHOUSDe. This affected the price recorded by the sUSDe oracle, which in turn changed the collateral requirements for loans in the protocol. The attacker used these altered requirements to take out insufficiently collateralized loans, allowing them to default on the loans and run off with the borrowed funds.
Related: What are flash loans in DeFi?
Some $14.4 million worth of drained funds were sent to an account ending in EB70, and another $4.6 million were transferred to an account ending in 5EB6. The stolen loot consists entirely of Ether (ETH), as the attacker swapped all other tokens for ETH immediately following the attack.
On June 12, the UwU team announced that it had paid back the bad debt for Tether (USDT), DAI, and crvUSD, allowing these markets to relaunch.
Related: UwU Lend Hit by $20m Hack
However, on the day after this announcement, Cyvers announced that the attacker had executed a second exploit against UwU Lend. This second attack targeted the uDAI, uWETH, uLUSD, uFRAX, uCRVUSD, and uUSDT pools, draining $3.7 million from them.
The exploit of UwU Lned had knock-on effects, which ended with the Curve CRV token going into freefall and its multiple-mansion-owning founder, Michael Egorov, liquidated for a $140 million stablecoin position.
This led to news reports stating that Egorov has proposed burning 10% of the CRV token supply, valued at $37 million, to help stabilize the token’s price.
Sadly, the burn story was a hoax tweeted by an Egorov impersonator attempting to phish users. The real Egorov told Cointelegraph:
“This information was tweeted by a fake (impersonator) account, accompanied by a scam link. Few journalists did not fact-check the news and published news about this.”
Deepfake scams: OKX user loses $2m
According to a translated report from Chinese crypto media outlet Wu Blockchain, one OKX user lost over $2 million from a deepfake scam generated through artificial intelligence (AI). The attackers purchased Lai J. Fang Chang’s personal data on Telegram and used it to create a “video application synthesized by AI to change mobile phone number.”
The video reportedly tricked staff on the OKX platform into authorizing changes to Chang’s password, email address and Google Authenticator device, bypassing all two-factor authentication controls. The attackers then withdrew all of Chang’s crypto into wallet accounts under their control.
According to the report, OKX is currently investigating the attack.
Related: AI-driven crypto crime is only just beginning — Elliptic report
CEXs: SomaXBT claims hack coverup on Lykke exchange
On June 9, blockchain researcher SomaXBT accused Lykke exchange of hiding its $22 million loss from a June 4 hack. The researcher started looking into the matter after noticing that several Lykke users had complained of being unable to withdraw funds. The exchange had reportedly stated on Discord that the platform was undergoing maintenance.
But after investigating, SomaXBT discovered that over $19 million of Bitcoin (BTC) and ETH had been transferred from multiple wallet accounts into a new address, which he says implies that the exchange may have been hacked. The researcher claimed that Lykke was “still trying to hide this fact,” as five days had passed without the exchange making an official statement.
The following day, Lykke acknowledged the attack and expressed apologies to its users for the inconvenience of not being able to withdraw. It also promised to repay all users, claiming that it has “solid capital reserves and a diverse portfolio” with which to do this.
Related: Lykke crypto exchange acknowledges hack after halting withdrawals
week.

The post Crypto-Sec: $11M Bittensor phish, UwU Lend and Curve fake news, $22M Lykke hack appeared first on Cointelegraph Magazine.