When a DeFi platform is hacked, suspicion often falls on insiders who are the most familiar with the smart contracts and security procedures and are, therefore, most likely to be able to devise an exploit. But are insiders really responsible for most DeFi hacks?
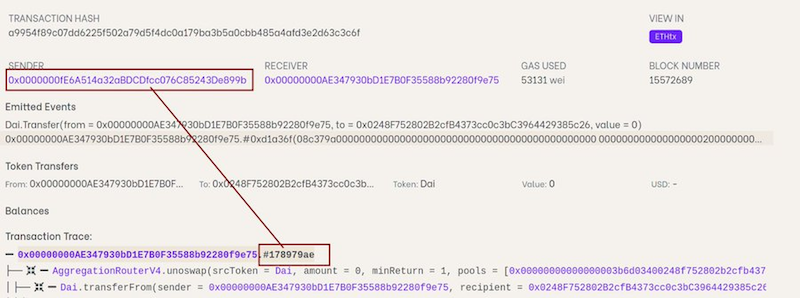
It seemed like a major scoop for on-chain sleuth Librehash. In September 2022, he reported that a $160-million hack of Wintermute, a U.K.-based DeFi platform, was likely an inside job.
It exploited a bug in a smart contract that Wintermute used to generate vanity wallet addresses.
According to Librehash (real name James Edwards), in a lengthy analysis of the hack, the relevant transactions initiated by the externally owned address (EOA) that made the call on the compromised smart contract “make it clear that the hacker was likely an internal member of the Wintermute team.”
“The knowledge required to execute this hack precludes the possibility that the hacker was a random, external entity.”
The hack “was the product of an inside job rather than an outside attacker exploiting an EOA with a weak private key,” the sleuth concluded in a tweet.
But what seemed like an open-and-shut case to Librehash was not simple to prove to the world at large. Wintermute, an automated market maker (AMM), vehemently rejected his theory, stating that it emanated from “an unsubstantiated rumor from a Medium page that has factual and technical inaccuracies associated with the claims made.”
And blockchain security firm BlockSec wrote an analysis of Librehas’s analysis, concluding that “the report is not convincing enough to accuse the Wintermute project.”
Conclusive proof of inside jobs is tricky
It’s not that surprising that Librehash’s report, despite its technical specificity, has not gone unchallenged.
In the murky world of DeFi hacks, few have been definitively attributed to insiders. There’s been plenty of suspicion and conjecture about inside jobs and speculation as to how deep the problem goes, but to date, pinning a hack on an insider has often been like trying to pin a tail on a fast-moving donkey.
“The anonymity provided by blockchain systems, coupled with the misuse of privacy-enhancing services like Tornado Cash by malicious actors, makes it challenging to ascertain the identities of these culprits,” says Lei Wu, chief technology officer of BlockSec.

There are some well-known examples of insiders allegedly behaving badly. John Karony, CEO of SafeMoon, and two colleagues were arrested last month for allegedly looting the Utah crypto firm for “millions of dollars” worth of its tokens to purchase luxury vehicles and real estate. NFT creator Remilia Corp, meanwhile, disclosed in September that a developer who worked on its Bonkler collection “took steps that allowed him to divert” more than $1 million in its generated fees.
“Clearly, there have been many projects that were rugged,” says Neville Grech, co-founder of blockchain security firm Dedaub, referring to “rug pulls” in which crypto developers drain their own projects of investor funds.
“Outside of rug pulls, there have been instances where projects were hacked a few hours after a fix has been made to a public codebase — but the fix wouldn’t have been deployed yet — so, probably, a keen follower of the project was involved.”
The transparency of DeFi means that with a bit of work, any sufficiently skilled cybercriminal can identify holes in the contracts. Chainalysis noted in its 2023 Crypto Crime Report that this transparency was “what makes DeFi so vulnerable — hackers can scan DeFi code for vulnerabilities and strike at the perfect time to maximize their theft.”
But when it comes to exploiting such opportunities, says Grech, insiders have “knowledge advantages such as access to unverified code, security assessments and deep technical knowledge about the project’s operation and potential weaknesses.”
However, he adds, this is a double-edged sword. “Insiders can be more easily discovered since team members would be close to them and can more easily second-guess their actions.”
Other hacks where insiders are suspected
DeFi hacks that have been attributed to insiders include the following:
In December 2022, DeFi protocol Ankr announced that the wallet of its aBNBc smart contract deployer had been compromised, allowing the hacker to mint six quadrillion aBNBc tokens, which were eventually converted into roughly $5 million. According to Ankr, “A former team member (who is no longer with Ankr) acted maliciously to conduct a combination of a social engineering and supply chain attack, inserting a malicious code package that was able to compromise our private key once a legitimate update was made.”
Ankr said it was working with law enforcement “to prosecute the former team member and bring them to justice. Unfortunately, internal bad actors can affect any protocol and we are working … to strengthen our security posture going forward.” To date, no charges appear to have been brought, and Ankr co-founders Stanley Wu and Chandler Song did not respond to requests for comment on the status of the case.
iToken suspicions
In October, blockchain security firm PeckShield alerted that crypto wallet iToken, formerly known as Huobi Wallet, “was suspected to have been drained” of about $260,000 in user funds, which the hacker converted to approximately 2.9 million in TRX tokens before transferring them to crypto exchanges ChangeNOW and Binance. The community speculated that an insider was to blame, in part because, three weeks earlier, Chinese media had reported that iToken user mnemonics and private keys had been hacked by a former employee, resulting in a $1.39-million loss. “The employee has been investigated by the police,” on-chain sleuth Wu Blockchain reported.
After Boy X Highspeed, a decentralized cross-chain exchange, disclosed in October 2021 that it had been robbed of $139 million, CEO Neo Wang said the hack was possibly an inside job in which an employee compromised an administrator’s private key by infecting BXH’s platform with a virus and then used the key to break into its BNB Smart Chain address. According to Wang, BXH had filed a case with a Chinese police unit that investigates digital crime. The outcome of the case is still unknown.
DeFi hacking is a growing business
There’s no doubt that DeFi platforms have been a happy hunting ground for crypto hackers in general. According to Chainalysis, DeFi projects accounted for 82.1%, or $3.1 billion, of the record $3.8 billion stolen by hackers in 2022. That’s an increase from the 73.3% recorded in 2021.
DeFi hacks outnumbered non-DeFi hacks by a ratio of 3.5:1, with a $625-million exploit of the gaming-focused Ronin Network bridge being the largest ever.
The surge in DeFi hacking reflects, in part, the explosive growth of the sector. Before falling off during the bear market, the total value locked in DeFi protocols rose 1,222% in 2021 to $247.8 billion, according to analytics platform DefiLlama.

So, who is carrying out these hacks? North Korea-linked hackers, such as those in the Lazarus Group cybercriminal syndicate, are a big factor. North Korea is “one of the driving forces behind the DeFi hacking trend that intensified in 2022,” Chainalysis reported.
And, of course, there are plenty of shadowy coders with the skills to attack a protocol.
In a recent external hack, U.S. authorities in July charged Shakeeb Ahmed, a former security engineer at Amazon, with using his technical skills to steal millions in assets from a decentralized crypto exchange in 2022. He pleaded guilty this week and will have to forfeit $12.3 million in cryptocurrency and face up to five years in jail.
Vulnerabilities in the self-executing code, or smart contracts, on DeFi blockchain platforms “range from traditional issues like integer overflow and re-entrancy bugs to logic bugs that are unique to DeFi protocols,” Wu says. Insiders are intimately familiar with many of these vulnerabilities, but the vulnerabilities can be found by external actors, too.
The most obvious cybercrimes by insiders come in the form of “rug pulls.”
“Almost every single day, there are small ‘rug pulls,’” says Richard Ma, CEO of blockchain security firm Quantstamp.
“The media and Crypto Twitter tend to discuss the larger hacks but not these small rug pulls that are in the tens of thousands of dollars.”
In such hacks, Ma explains, a project creator “uses a backdoor in the smart contract to mint tokens and sell them into Uniswap or uses a backdoor to steal the funds.”
The curious case of Multichain
What may have been one of the larger rug pulls came to light in July when Multichain, a platform that facilitates cross-chain transactions, announced on Twitter that it had ceased operations after user assets locked on its multi-party computation (MPC) addresses “were transferred to unknown addresses abnormally.”

The somewhat cryptic announcement also said Multichain had lost access to its MPC node servers the previous May after its CEO, Zhaojun He, was arrested by Chinese police. The servers, it said, were running under Zhaojun’s personal cloud server account, and no other member of the Multichain team had access to that account.
“Since the inception of the project, all operational funds and investments from investors have been under Zhaojun’s control,” Multichain said. “This also means that all the [Multichain] team’s funds and access to the servers are with Zhaojun and the police.”
According to Multichain, Zhaojun’s sister had also been arrested and was said to have “preserved” the remaining user assets by transferring them to wallets she controlled. “The status of the assets she has preserved is uncertain,” Multichain said.
Chainalysis estimated that more than $125 million in assets were drained in the hack. “While it’s possible [the MPC] keys were taken by an external hacker, many security experts and other analysts think this exploit could be an inside job or rug pull,” Chainalysis added.
Other theories, however, have been advanced for the Multichain hack. One is that Zhaojun was arrested and the assets were seized as part of a Chinese Anti-Money Laundering operation. Alternatively, says Grech, “a plausible explanation is that the founder of the project lost his private keys to (allegedly rogue) law enforcement officers” after he was arrested.
Chinese authorities haven’t shed any light on the Multichain mystery, and there have been no updates on the status of Zhaojun and his sister.
Whoever the Multichain culprits may be, the DeFi carnage is showing some signs of abating. In the first six months of this year, cybercriminals stole $480 million through smart contract DeFi hacks, down 75% from the same period in 2022, according to PeckShield. Blockchain analysis provider Elliptic said in a recent report that Lazarus Group’s “latest activity suggests that since last year, it has shifted its focus from decentralized services to centralized ones.”
But the insider threat remains a particularly insidious one for the DeFi sector. And Librehash stands by his analysis of the Wintermute hack. He said in a Telegram post:
“Nothing was debunked because this channel doesn’t publish conspiracy theories or push half-assed, poorly researched ideas for the sake of generating clicks, views or otherwise.”
week.

The post DeFi’s billion-dollar secret: The insiders responsible for hacks appeared first on Cointelegraph Magazine.