Metaversal is a Bankless newsletter for weekly level-ups on NFTs, virtual worlds, & collectibles
Dear Bankless Nation,
Sky Mavis, the creators of leading NFT game Axie Infinity, have been blindsided by a huge hack.
The team stewards the infrastructure that underpins the Ronin bridge, which lets users send crypto back and forth between Ethereum and Axie’s Ronin sidechain.
However, last week that infrastructure was compromised by a blackhat attacker to the tune of ~$625M, making the incident the largest crypto hack so far according to Rekt’s infamous leaderboard.
Let’s catch up on what we know so far about the attack for today’s Metaversal.
-WMP
🙏 Sponsor: Unstoppable Domains – Your name, universal wallet address, and login for web3.
The Ronin bridge attack
What happened
-
The Ronin sidechain is currently secured by nine validator nodes. On Wednesday, March 23rd, an attacker or group compromised five of these nodes.
-
Then the attacker used the nodes’ signatures to withdraw 173.6k ETH and 25.5M USDC, or ~$625M in USD terms at current prices, from the Ronin bridge.
-
Fast forward to March 29th, and one user’s inability to withdraw 5k ETH via the Ronin bridge alerted the Sky Mavis team that funds had been drained from the bridge last week.
-
Sky Mavis responded by pausing the bridge and Ronin’s Katana exchange. The team is also migrating its node infrastructure and engaging with law enforcement, large crypto exchanges, and Chainalysis to encircle the culprit as best as possible. All funds on the Ronin sidechain proper are currently safe.
The big idea
-
The Ronin bridge hack wasn’t the result of a smart contract exploit in contrast to some other recent bridge attacks, e.g. the $325M breach of the Solana Wormhole bridge in Feb. 2022. Rather, the Ronin bridge attack resulted from a multi-signature compromise, as Optimism software engineer Kelvin Fichter has noted. The actual vector of the compromise remains unclear, although a bug in the Ronin validator client software seems likely.

This is very different from previous bridge hacks where the root cause was a smart contract bug. This is a much more “classical” hack of private keys in a multi-key security setup. This is why trust-minimized bridging is SO important.
The specter of validator-based bridges
-
With nine validator nodes, Ronin needs five nodes to stay honest at all times in order to remain secure. This bridge attack was catastrophic because in one fell swoop the attacker was able to compromise five nodes at once, so their withdrawals became illicitly “honest,” as it were.
-
Accordingly, more nodes spread out across more community-run or third-party projects in combination with multiple software clients would’ve presumably prevented the hack. Easier said than done, though, and hindsight’s 20/20 right. For now, Sky Mavis has raised Ronin’s validator threshold from five to eight, yet it’s also safe to assume they’ll look at further decentralizing and increasing total validators.
-
Zooming out, look for the Ronin bridge attack to spur more attention and development around trust-minimized or “trustless” bridges around the wider cryptoeconomy going forward.
The Ronin recovery
-
“We are in the process of discussing with Axie Infinity / Sky Mavis stakeholders about how to best move forward and ensure no users’ funds are lost,” the Ronin bridge attack announcement said. “Sky Mavis is here for the long term and will continue to build.”
-
Adam Cochran, a partner at Cinneamhain Ventures, posited that Sky Mavis might end up selling equity to cover the losses from the attack, though that’s just speculation for now.

3/6
And to raise enough to cover this from equity, would probably mean selling 20%-30% of Sky Maven (assuming discount on last $3B valuation, as this capital is used for recovery and not growth, so would be a down round)
The laundering question
-
Looking closely at the attacker’s addresses (e.g. 1, 2, and 3), we can see that the vast majority of the stolen funds are still sitting in the “Ronin Exploiter 1” address.
-
However, in tracing transactions to the other wallets we can see that the attacker sent some batches of ETH to centralized crypto exchanges like FTX and Crypto.com to test if they could cash out to fiat.
<div class="tweet" data-attrs="{"url":"https://twitter.com/FrankResearcher/status/1508832517826174989","full_text":"Imagine stealing 600 million 6 days ago and depositing money on @FTX_Officialnn ","username":"FrankResearcher","name":"Igor Igamberdiev","date":"Tue Mar 29 15:44:39 +0000 2022","photos":[{"img_url":"https://pbs.substack.com/media/FPBzIdgWQAsz38-.jpg","link_url":"https://t.co/YGzr7uyk5Q","alt_text":null}],"quoted_tweet":{"full_text":"The Ronin bridge has been exploited for 173,600 Ethereum and 25.5M USDC.nnThe Ronin bridge and Katana Dex have been halted.","username":"Ronin_Network","name":"Ronin"},"retweet_count":324,"like_count":1388,"expanded_url":{},"video_url":null}”>

Imagine stealing 600 million 6 days ago and depositing money on @FTX_Official
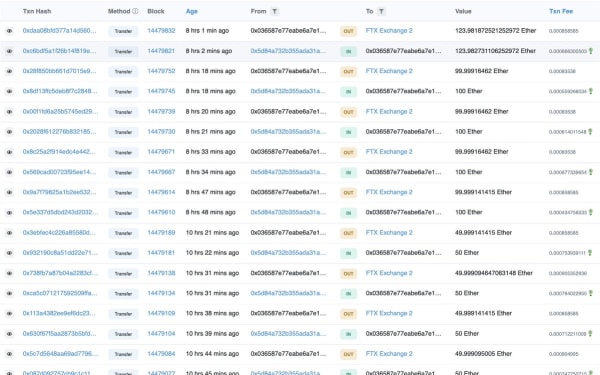
Ronin @Ronin_Network
The Ronin bridge has been exploited for 173,600 Ethereum and 25.5M USDC.
The Ronin bridge and Katana Dex have been halted.
-
Lately, most blackhat hackers in the Ethereum ecosystem will mix their stolen ETH through privacy solution Tornado Cash to “clean” the funds. Accordingly, it seems unusual that the attacker sent funds straight to centralized crypto exchanges without first mixing via Tornado. In response, some analysts have raised the possibility that the culprit purchased other users’ exchange accounts to make surreptitious withdrawals.

I’m 99% sure that the hacker is someone seasoned with a lot of cybersecurity experience (not a crypto degen kid).
It’s naive to think that such an attacker will transfer money to his own accounts on CEX like FTX or Crypto.
It’s either a honeypot or they are using money mules.
-
The jig is up now, though, as all major crypto exchanges are now monitoring the attackers’ main addresses and will look to stop any cash outs from them. This means the exploiter may have to adapt their ways, e.g. using Tornado or trying to rinse ETH through NFT buy-and-sells, to make further headway. Still, trying to launder +$600M in crypto is a massive undertaking.
My takeaway
-
The Ronin bridge attack was a major setback for the Axie ecosystem. Yet if there’s any team-community combo that can bounce back from this hack and be stronger for it, it’s Sky Mavis and the Axie Infinity community. In the meantime, many of us will be watching the chain to see what the attacker does next with the stolen crypto.
Action steps
-
🚨 Read the Ronin validators compromise announcement
-
🐂 Read my previous write-up NFT bull run ‘22 if you missed it
Author Bio
William M. Peaster is a professional writer and creator of Metaversal—a Bankless newsletter focused on the emergence of NFTs in the cryptoeconomy. He’s also recently been contributing content to Bankless, JPG, and beyond!
Subscribe to Bankless. $22 per mo. Includes archive access, Inner Circle & Badge.
🙏Thanks to our sponsor
UNSTOPPABLE DOMAINS
Your Unstoppable Domain is all you need to verify your identity and access the decentralized web. And now with Humanity Check, you can prove that you’re, well, you – without revealing personal data. No matter where you go on the web, you’ll have total control over which apps you want to share data with…and which ones you don’t.
👉 Get your name for as low as $5 here.
👉 Head to Unstoppabledomains.com
Not financial or tax advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. This newsletter is not tax advice. Talk to your accountant. Do your own research.
Disclosure. From time-to-time I may add links in this newsletter to products I use. I may receive commission if you make a purchase through one of these links. Additionally, the Bankless writers hold crypto assets. See our investment disclosures here.





