Metaversal is a Bankless newsletter for weekly level-ups on NFTs, virtual worlds, & collectibles
Dear Bankless Nation,
On Monday, March 21st, Arthur Cheong — a.k.a. Arthur0x, the founder of DeFiance Capital — faced a wallet compromise.
In the wake of the breach, the attackers responsible sold off dozens of choice NFTs on OpenSea and illicitly raised ~600 ETH, or +$1.7M, in the process.
Cheong has since revealed the email he believes launched the spear phishing exploit. Upon closer inspection, the email and the attack follow the recent modus operandi of the BlueNoroff hacker group.
The BlueNoroff team is akin to a financial crimes unit within the North-Korea linked Lazarus Group, researchers have noted. I lay out why they’re the main suspects in the heist of Cheong’s NFTs for today’s Metaversal.
-WMP
🙏 Sponsor: Unstoppable Domains – Your name, universal wallet address, and login for web3.
Attack of the APT, or Advanced Persistent Threat
What happened
-
Circa 9PM ET on Monday, an attacker started scraping NFTs and ERC20 tokens from one of Arthur Cheong’s hot wallets, i.e. software wallets on a computer or mobile device, into their own wallet. Later another one of Cheong’s wallets was targeted as well.
<div class="tweet" data-attrs="{"url":"https://twitter.com/robbyhammz/status/1506083300602961926","full_text":"ATTENTION ALL @AzukiZen it seems sadly @Arthur_0x wallet has been hacked please do not bid or buy any of these NFTs from this address!!! ","username":"robbyhammz","name":"StockEd NFT’s","date":"Tue Mar 22 01:40:15 +0000 2022","photos":[{"img_url":"https://pbs.substack.com/media/FOaux39XoAE2PKM.jpg","link_url":"https://t.co/SsdKt8otis","alt_text":null},{"img_url":"https://pbs.substack.com/media/FOaux39XoAMwLxS.jpg","link_url":"https://t.co/SsdKt8otis","alt_text":null}],"quoted_tweet":{},"retweet_count":120,"like_count":314,"expanded_url":{},"video_url":null}”>

ATTENTION ALL @AzukiZen it seems sadly @Arthur_0x wallet has been hacked please do not bid or buy any of these NFTs from this address!!!
-
The attacker accrued nearly 60 NFTs in this manner and proceeded to sell many of them on OpenSea before most people in the community had realized what was happening.
<div class="tweet" data-attrs="{"url":"https://twitter.com/PeckShieldAlert/status/1506110131259736071","full_text":"#PeckShieldAlert @Arthur_0x ’s hot wallet appears to be compromised. ~59 #NFTs was transferred to etherscan.io/address/0xe47e… , including ~5 #CloneX, ~17 $Azuki @AzukiZen, ~2 @TabinekoKIKI, ~2 @HedgiesOfficial, ~33 @SecondSelfNFTn~19 stolen NFTs wiped for ~233 $ETH (~$690k). ","username":"PeckShieldAlert","name":"PeckShieldAlert","date":"Tue Mar 22 03:26:52 +0000 2022","photos":[{"img_url":"https://pbs.substack.com/media/FObG_8BaIAE-3kH.png","link_url":"https://t.co/oqM08ex1Yg","alt_text":null}],"quoted_tweet":{},"retweet_count":17,"like_count":48,"expanded_url":{},"video_url":null}”>

#PeckShieldAlert @Arthur_0x ’s hot wallet appears to be compromised. ~59 #NFTs was transferred to etherscan.io/address/0xe47e… , including ~5 #CloneX, ~17 $Azuki @AzukiZen, ~2 @TabinekoKIKI, ~2 @HedgiesOfficial, ~33 @SecondSelfNFT
~19 stolen NFTs wiped for ~233 $ETH (~$690k).
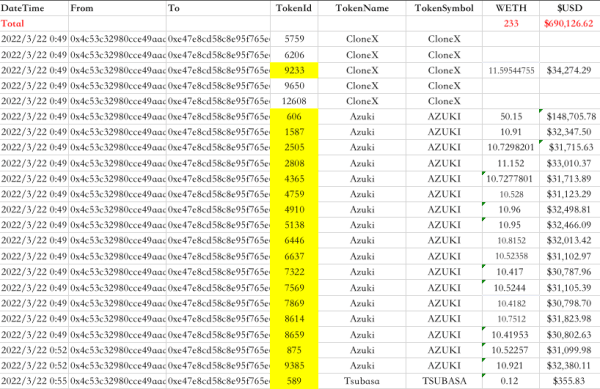
-
The attacker supplemented their NFT sales by selling ERC20 tokens like WETH and LOOKS on decentralized exchanges like 1inch. At press time, the wallet Etherscan has since designated Arthur0x Wallet Hacker was sitting on an illicit trove of ~590 ETH.
-
A longtime veteran of crypto and DeFi, Cheong was initially at a loss for how the attack vector occurred. However, in working with some colleagues Cheong was able to determine that the attachment in this forwarded, visually normal email was likely the culprit:

Found out the likely root cause for the exploit, it’s a targeted social engineering attack. Received a spear-phishing email that really seems to be sent by one of our portco with content that seems like general industry-relevant content.
They are likely targeting all crypto peep
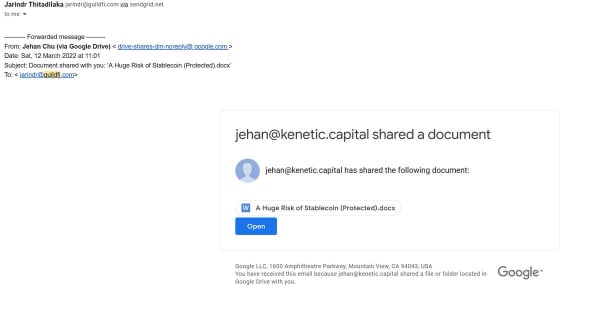
-
Cheong went on to assert that the BlueNoroff team of Lazarus Group was behind the hack. He also alleged the same attackers were behind other major crypto hacks in recent times:

Have strong evidence to believe this is the same group of hackers that exploited BZX, Hugh, MGNR and myself.
The infamous Lazarus group.
What is BlueNoroff?
-
Per the Kaspersky article Cheong posted about BlueNoroff, researchers coined the phrase “BlueNorOff” to describe an Advanced Persistent Threat (APT) team they discovered while investigating the major Bangladesh Bank cyberattack of Feb. 2016.
-
Kaspersky has repeatedly noted the APT is connected to Lazarus Group and has “an usual financial motivation for an APT.” Analyses suggest the team functions “like a unit within a larger formation of Lazarus attackers, with the ability to tap into its vast resources: be it malware implants, exploits, or infrastructure.”
-
While BlueNoroff previously targeted mainstream banking institutions, its offensive focus has apparently shifted toward cryptocurrency companies and high-profile crypto figures in recent years.
-
Prior to Cheong’s wallet hacks, BlueNoroff was seen to be active as recently as Nov. 2021. In 2020 the U.S. Army estimated the organization had approximately 1,700 contributors. The group is sizable, experienced, and specializes in all sorts of tactics like phishing.
Analyzing the attack
-
The Arthur Cheong hack is perfectly in line with a recent BlueNoroff attack style. This vector first starts with stalking, i.e. BlueNoroff studies a cryptocurrency organization’s persons of interest and how they interact.
-
They then learn how to mimic, spear phish, normal interactions within and around that organization, i.e. forwarding a tainted email in an otherwise seemingly normal interaction.
-
The technical vector, e.g. a document shared through Google Drive, allows BlueNoroff to run malware to infect and ascertain access to victims’ devices.
-
In review, Cheong was likely stalked for weeks or even months. He was then spear phished via what looked like a benign forwarded email from one of his crypto colleagues. Malware then allowed attackers to compromise hot wallets on Cheong’s devices, which they scraped NFTs and ERC20s from to sell.
-
We certainly won’t be getting a confession from the BlueNoroff team as to their involvement. That said, in light of all the available facts I think it’s fair to say BlueNoroff is Suspect #1 at this time. The attack fits their recent modus operandi to a tee. Of course, sometimes APTs mimic the styles of other APTs to cover their own tracks, but Occam’s razor tells us to look at BlueNoroff for now. Lazarus Group and North Korea have major incentives and major capabilities to conduct such attacks, to say the least.
Zooming out: what should you do?
-
Hardware wallets (physical devices that stay disconnected from the internet at all times) aren’t perfect crypto security solutions, but they absolutely would’ve been a great starting point for making Cheong’s NFTs that much harder to steal in this case. Never store NFTs of non-trivial value in hot, i.e. internet-connected, software wallets.
-
Cheong was a high-profile target in the crypto ecosystem, but in the wake of an incident like this I think it’s worthwhile for everyone to review and if needed improve upon their crypto OpSec, or operational security, since it’s clear APT-level actors are on the hunt. Some awesome guides I’ve seen on crypto OpSec include:
-
Self-custody OpSec Tips by Jason Choi
-
Crypto OpSec SelfGuard Roadmap by OffcierCia
-
Ultimate Guide to Storing Your Bitcoin and Cryptocurrencies by Ken Chia
-
How to Store Your Crypto Wallet on a Virtual Machine by P. Misirov (Advanced)
-
-
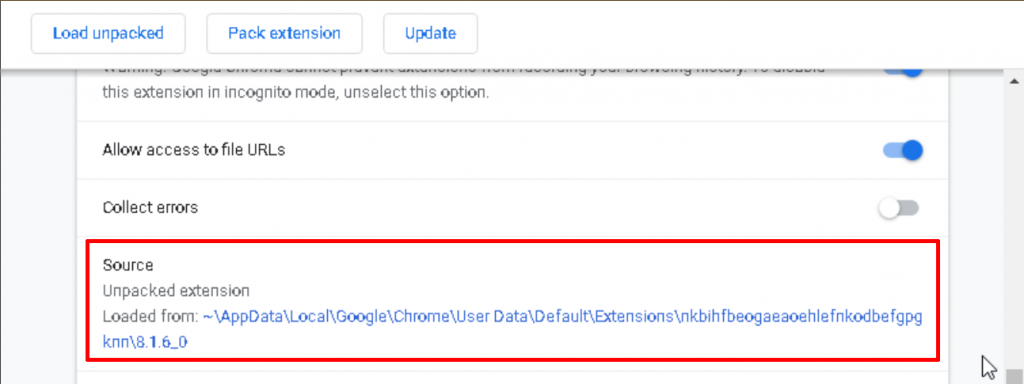
Worried that you may have malware on your computer and want to see if your MetaMask browser extension has been injected with malicious code? There’s a trace you can look for. For example, in Chrome you could go to your Extensions center and check to see that the “Source” of your MetaMask wallet says “Chrome Web Store.” If it looks like something below and you’re not personally responsible for the change, the extension your MetaMask extension may be compromised.
Action steps
-
🔒 Review your crypto/NFT OpSec
-
🌌 Read my latest tactic A beginner’s guide to Cosmos in Bankless
Author Bio
William M. Peaster is a professional writer and creator of Metaversal—a Bankless newsletter focused on the emergence of NFTs in the cryptoeconomy. He’s also recently been contributing content to Bankless, JPG, and beyond!
Subscribe to Bankless. $22 per mo. Includes archive access, Inner Circle & Badge.
🙏Thanks to our sponsor
UNSTOPPABLE DOMAINS
Your Unstoppable Domain is all you need to verify your identity and access the decentralized web. And now with Humanity Check, you can prove that you’re, well, you – without revealing personal data. No matter where you go on the web, you’ll have total control over which apps you want to share data with…and which ones you don’t.
👉 Get your name for as low as $5 here.
👉 Head to Unstoppabledomains.com
Not financial or tax advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. This newsletter is not tax advice. Talk to your accountant. Do your own research.
Disclosure. From time-to-time I may add links in this newsletter to products I use. I may receive commission if you make a purchase through one of these links. Additionally, the Bankless writers hold crypto assets. See our investment disclosures here.